Become a MacRumors Supporter for $50/year with no ads, ability to filter front page stories, and private forums.
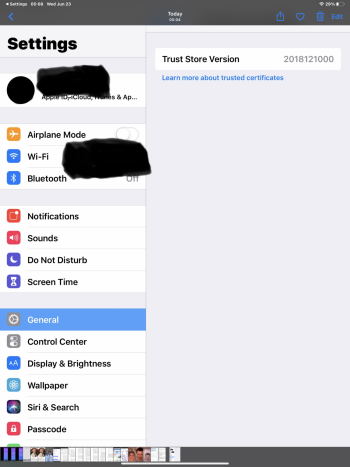
iPhone Can anyone tell me what "trust asset version" means?
- Thread starter mebehere
- Start date
- Sort by reaction score
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Can someone, anyone, just check their settings and let me know what they see?
Seriously. Anyone. It’s easy to do.
Thanks.
I have the same. Am I supposed to tell you that? lol.
I have iOS 14.2 RN, my trusted asset version is 9. I contacted Apple when I first noticed the “Trust Asset Version 7” on another device approx 1 yr ago. After being transferred, on hold etc. for a while the “senior” advisor attempted to locate any info on the subject.
I was told the Asset version has to do with a new internal rating for Apple Pay/wallet calculating the likelihood of fraud to occur on the device. My carrier Sprint was dumbfounded when I asked them. They thought it was something to do with the finance industry “asset”. So honestly who knows! I had pretty bad issues with my XS Max in 2018 regarding very strange certificates (SSL/TLS) and APN ( push cert) that was never resolved so I don’t bother asking Apple anymore or writing on the Apple forum because NO ONE COULD EVER HACK AN IPHONE! right- lol
I scour the Internet/ Dev areas usually.
Best regards!
I was told the Asset version has to do with a new internal rating for Apple Pay/wallet calculating the likelihood of fraud to occur on the device. My carrier Sprint was dumbfounded when I asked them. They thought it was something to do with the finance industry “asset”. So honestly who knows! I had pretty bad issues with my XS Max in 2018 regarding very strange certificates (SSL/TLS) and APN ( push cert) that was never resolved so I don’t bother asking Apple anymore or writing on the Apple forum because NO ONE COULD EVER HACK AN IPHONE! right- lol
I scour the Internet/ Dev areas usually.
Best regards!
Bro i started on 7 years ago now im a TAv12 lol and been researching since 7. I can confirm that this is NOTHING NICE. the troubles i have had to go thru with apple and even phone carrier who was forcing certs on me both refuse to answer my questions or remove the certificates that they forced on after i purchased it. I am still fighting them on it 2 years later and may have to take it to court with the substancial proof i have and other victims. Look in ur analytic data and copy paste a full page of one of them to ur notes then click find in page and type "pegasus" i want to see how many of yall have that nastyness forced into ur device as well like i do. Never be quiet we need more to stand up because the ppl who mock us who may even know way more about tech than us couldnt be anymore wrong and i have had confirmation in various forms about this issue and how bad they are trying to hide and ignore it. If it was so normal why is it so hard to find documentation by apple on it? Why wont they answer on phone bout it.? Why doesnt anyone know like actually know lots about it? But we all can find out when the last time our phones passed gas or how many minutes our sex lives contain a day/ heart beat? Come one...
-bird
-bird
My phone shows “trust asset version 11.” I’ve bought many new phones since 2012 bc they have been compromised, but it keeps on happening to me. I know who is goi g this, but I don’t know how to make it stop. I would be thrilled to join a lawsuit with others. Please contact me, but keep in mind you may need to try several times, as I have no “safe” device to ensure your attempt won’t be twarted.
Not sure why everyone is freaking out about this? This is a trusted root certificate store. Every OS has some implementation of this. This allows the OS to communicate securely to SSL enabled websites.
There’s even a link on that settings page explaining this
 support.apple.com
support.apple.com
There’s even a link on that settings page explaining this
Available trusted root certificates for Apple operating systems - Apple Support
Trust Stores contains trusted root certificates that are preinstalled with iOS, iPadOS, macOS, tvOS, and watchOS.
I understand what the Trust Store does. I don’t understand what is meant by “Trust Asset Version .” I have a generic understanding of what Secure Socket Layer is. I can’t find anything that explains what “TRUST ASSET VERSION” means, and why many people don’t have one listed in their iPhone. Trust Store, I get. I would really like an explanation of TRUST ASSET VERSION, please.
THANKS!!
THANKS!!
This is on everyone’s phone. So many things wouldn’t work without it. The version number is just that. Certificates are periodically updated or removed so they create a new version of the bundle of certificates.I understand what the Trust Store does. I don’t understand what is meant by “Trust Asset Version .” I have a generic understanding of what Secure Socket Layer is. I can’t find anything that explains what “TRUST ASSET VERSION” means, and why many people don’t have one listed in their iPhone. Trust Store, I get. I would really like an explanation of TRUST ASSET VERSION, please.
THANKS!!
Thank you very much for differentiating between the two separate yet interrelated entities. I follow and understand your explanation, all up to one little part...not all iPhones have a “TRUST ASSET VERSION.” Unfortunately, that’s what leaves me still unsettled. I mean no disrespect toward you at all. Either way, thx for responding.This is on everyone’s phone. So many things wouldn’t work without it. The version number is just that. Certificates are periodically updated or removed so they create a new version of the bundle of certificates.
I have never seen an iPhone or iPad without it. Can you provide a screenshot of one without it?Thank you very much for differentiating between the two separate yet interrelated entities. I follow and understand your explanation, all up to one little part...not all iPhones have a “TRUST ASSET VERSION.” Unfortunately, that’s what leaves me still unsettled. I mean no disrespect toward you at all. Either way, thx for responding.
Hi everyone. This is my first post but I have been lurking and learning for a long time. I’m happy to provide that screenshot and some additional information I’ve learned in the 2 years of hell I’ve been through since my small business was a victim of a cyberattack (August 2019). Eventually all of my devices became infected and like the stories I’ve read here and elsewhere, I’ve had to replace key devices multiple times.
During the 2 years since the attack I have documented MANY (as in >25 to be conservative) iOS attack-related behaviors (Windows too many to count but definitely > 100) that I was able to isolated specifically to Apple-delivered applications (accessibility settings, Games, Screen Time, Mail, iCloud, Files, to name a few) by capturing this behavior on a device that contained only factory-installed Apple apps.
I’ve also searched as many forums as I could find for postings describing behaviors like the ones I’ve been trying to mitigate and every time I would find one it would be followed by derogatory, degrading and judgements comments to or about the OP. So I have stayed silent until now. I am only now coming forward because Apple’s multiple zero-day WebKit bug fixes released since the beginning of the year have eliminated most of my issues.
Needless to say I am beyond elated to have control back over my devices, but unfortunately am having to work through a lot of unexpected, I guess one would call it, PTSD. Like explained in posts by others, I have experienced almost two years of near-constant phone intrusions (eavesdropping and dropped calls), observation (pics taken of me when I was alone and before I covered all lenses), rogue certificates, hijacked files that were hidden and when found unable to be deleted (type a space in the Files app search field), lost clients and personal relationships, interactive screen “battles” with the bad actor over files and screen time settings, and on and on. So please don’t dismiss these claims as baseless because I assure you I have been extremely thorough in documenting everything I mention in this post.
A few other facts:
1) the appearance of Asset Trust Version 8 was one of the consistent indicators that my device had become infected either after purchasing the device or after a complete wipe via DFU. The second consistent indicator was the appearance of rogue certificates not linked to a profile that i could only find by starting to create a VPN connection via certificates (the Cisco choice) and viewing available certificates by clicking on the certificate field. This was on a device that had no VPN app nor any profiles displayed.
2) In the initial download and upgrade to iOS 13, I saw that the option to select Cisco VPN certificates was no longer possible - which makes sense since I did not have a Cisco VPN installed past or present. And voila, Asset Trust Version xx now appeared on everyone’s iOS devices. Prior to that the field was not present on my devices (as shown on my screen print) until the device was compromised. So for a year my two consistent indicators that my device was infected was removed with the upgrade to iOS 13. Unfortunately the problems seemingly tied to those two indicators did not disappear.
3) I’ve reported these and many other issues to Apple but either the tickets were closed without resolution or notifying me, or I would be given false or misleading information such as was with the 3 or 4 times I called about Asset Trust Version 8.
4) My devices were always updated the day an update was available.
I hope that others in the seemingly small group who have reported these intrusions have also found peace and privacy after applying the 14.x security updates for the Apple (pseudo-admitted) zero-day iOS and MacOS bugs.
During the 2 years since the attack I have documented MANY (as in >25 to be conservative) iOS attack-related behaviors (Windows too many to count but definitely > 100) that I was able to isolated specifically to Apple-delivered applications (accessibility settings, Games, Screen Time, Mail, iCloud, Files, to name a few) by capturing this behavior on a device that contained only factory-installed Apple apps.
I’ve also searched as many forums as I could find for postings describing behaviors like the ones I’ve been trying to mitigate and every time I would find one it would be followed by derogatory, degrading and judgements comments to or about the OP. So I have stayed silent until now. I am only now coming forward because Apple’s multiple zero-day WebKit bug fixes released since the beginning of the year have eliminated most of my issues.
Needless to say I am beyond elated to have control back over my devices, but unfortunately am having to work through a lot of unexpected, I guess one would call it, PTSD. Like explained in posts by others, I have experienced almost two years of near-constant phone intrusions (eavesdropping and dropped calls), observation (pics taken of me when I was alone and before I covered all lenses), rogue certificates, hijacked files that were hidden and when found unable to be deleted (type a space in the Files app search field), lost clients and personal relationships, interactive screen “battles” with the bad actor over files and screen time settings, and on and on. So please don’t dismiss these claims as baseless because I assure you I have been extremely thorough in documenting everything I mention in this post.
A few other facts:
1) the appearance of Asset Trust Version 8 was one of the consistent indicators that my device had become infected either after purchasing the device or after a complete wipe via DFU. The second consistent indicator was the appearance of rogue certificates not linked to a profile that i could only find by starting to create a VPN connection via certificates (the Cisco choice) and viewing available certificates by clicking on the certificate field. This was on a device that had no VPN app nor any profiles displayed.
2) In the initial download and upgrade to iOS 13, I saw that the option to select Cisco VPN certificates was no longer possible - which makes sense since I did not have a Cisco VPN installed past or present. And voila, Asset Trust Version xx now appeared on everyone’s iOS devices. Prior to that the field was not present on my devices (as shown on my screen print) until the device was compromised. So for a year my two consistent indicators that my device was infected was removed with the upgrade to iOS 13. Unfortunately the problems seemingly tied to those two indicators did not disappear.
3) I’ve reported these and many other issues to Apple but either the tickets were closed without resolution or notifying me, or I would be given false or misleading information such as was with the 3 or 4 times I called about Asset Trust Version 8.
4) My devices were always updated the day an update was available.
I hope that others in the seemingly small group who have reported these intrusions have also found peace and privacy after applying the 14.x security updates for the Apple (pseudo-admitted) zero-day iOS and MacOS bugs.
Attachments
Trust Store Version and Trust Asset Version are the exact same thing. They just broke the version information down a little more some time after iOS 12. See the screenshots. One is from iOS 12 and one is from iOS 14. Again, this has nothing to do with being infected with anything. It's part of the OS.Hi everyone. This is my first post but I have been lurking and learning for a long time. I’m happy to provide that screenshot and some additional information I’ve learned in the 2 years of hell I’ve been through since my small business was a victim of a cyberattack (August 2019). Eventually all of my devices became infected and like the stories I’ve read here and elsewhere, I’ve had to replace key devices multiple times.
During the 2 years since the attack I have documented MANY (as in >25 to be conservative) iOS attack-related behaviors (Windows too many to count but definitely > 100) that I was able to isolated specifically to Apple-delivered applications (accessibility settings, Games, Screen Time, Mail, iCloud, Files, to name a few) by capturing this behavior on a device that contained only factory-installed Apple apps.
I’ve also searched as many forums as I could find for postings describing behaviors like the ones I’ve been trying to mitigate and every time I would find one it would be followed by derogatory, degrading and judgements comments to or about the OP. So I have stayed silent until now. I am only now coming forward because Apple’s multiple zero-day WebKit bug fixes released since the beginning of the year have eliminated most of my issues.
Needless to say I am beyond elated to have control back over my devices, but unfortunately am having to work through a lot of unexpected, I guess one would call it, PTSD. Like explained in posts by others, I have experienced almost two years of near-constant phone intrusions (eavesdropping and dropped calls), observation (pics taken of me when I was alone and before I covered all lenses), rogue certificates, hijacked files that were hidden and when found unable to be deleted (type a space in the Files app search field), lost clients and personal relationships, interactive screen “battles” with the bad actor over files and screen time settings, and on and on. So please don’t dismiss these claims as baseless because I assure you I have been extremely thorough in documenting everything I mention in this post.
A few other facts:
1) the appearance of Asset Trust Version 8 was one of the consistent indicators that my device had become infected either after purchasing the device or after a complete wipe via DFU. The second consistent indicator was the appearance of rogue certificates not linked to a profile that i could only find by starting to create a VPN connection via certificates (the Cisco choice) and viewing available certificates by clicking on the certificate field. This was on a device that had no VPN app nor any profiles displayed.
2) In the initial download and upgrade to iOS 13, I saw that the option to select Cisco VPN certificates was no longer possible - which makes sense since I did not have a Cisco VPN installed past or present. And voila, Asset Trust Version xx now appeared on everyone’s iOS devices. Prior to that the field was not present on my devices (as shown on my screen print) until the device was compromised. So for a year my two consistent indicators that my device was infected was removed with the upgrade to iOS 13. Unfortunately the problems seemingly tied to those two indicators did not disappear.
3) I’ve reported these and many other issues to Apple but either the tickets were closed without resolution or notifying me, or I would be given false or misleading information such as was with the 3 or 4 times I called about Asset Trust Version 8.
4) My devices were always updated the day an update was available.
I hope that others in the seemingly small group who have reported these intrusions have also found peace and privacy after applying the 14.x security updates for the Apple (pseudo-admitted) zero-day iOS and MacOS bugs.


Last edited:
I’m not going to pretend to know what these fields mean, but I can say with assurance that prior to iOS 13 (my screen print was from an UNcompromised iPad Air 2 on the latest 12.x release) after checking with many other people, no one else had anything other than the Trust Asset Store - no Version.
Once upgraded to iOS 13, the Trust Asset Version field appeared below Trust Store on every iOS device of mine - both compromised and uncompromised - as well as those I asked who did not have it prior to iOS 13.
Again, I’m only stating my experience that prior to iOS 13 this field always appeared in conjunction with the rogue certificates (ones that didn’t start with “com.”) which would also be the day irregular behaviors began again. I witnessed this many times having factory-reset/DFU’ed my iOS devices multiple times prior to purchasing a new device. Only to see the cycle repeat on the new device within a day or two of purchase - and oftentimes never having been on Wi-Fi thinking using only cellular data might keep the device protected.
I would be very willing to accept that this is a part of iOS if a) Apple would have validated that it was legitimate and would have offered an explanation as to how it was used, or b) everyone had it in their devices prior to iOS 13.
Having spent hours researching and more hours fruitlessly trying to work with Apple, it seems only logical something is being concealed about the presence of this field prior to iOS 13 when it suddenly displayed on all updated devices.
Could someone point me toward documentation that describes the purpose of this field (prior to iOS 13) and also explain why it only appeared on some devices prior to 13? I would be very grateful and would pass it on to anyone else posting on a forum about the same concern.
However, even if documented somewhere I didn’t see, it’s always going to remain puzzling why Apple would not just have answered the question and put fears to rest for me and those who have reported similar concerns as mine.
Once upgraded to iOS 13, the Trust Asset Version field appeared below Trust Store on every iOS device of mine - both compromised and uncompromised - as well as those I asked who did not have it prior to iOS 13.
Again, I’m only stating my experience that prior to iOS 13 this field always appeared in conjunction with the rogue certificates (ones that didn’t start with “com.”) which would also be the day irregular behaviors began again. I witnessed this many times having factory-reset/DFU’ed my iOS devices multiple times prior to purchasing a new device. Only to see the cycle repeat on the new device within a day or two of purchase - and oftentimes never having been on Wi-Fi thinking using only cellular data might keep the device protected.
I would be very willing to accept that this is a part of iOS if a) Apple would have validated that it was legitimate and would have offered an explanation as to how it was used, or b) everyone had it in their devices prior to iOS 13.
Having spent hours researching and more hours fruitlessly trying to work with Apple, it seems only logical something is being concealed about the presence of this field prior to iOS 13 when it suddenly displayed on all updated devices.
Could someone point me toward documentation that describes the purpose of this field (prior to iOS 13) and also explain why it only appeared on some devices prior to 13? I would be very grateful and would pass it on to anyone else posting on a forum about the same concern.
However, even if documented somewhere I didn’t see, it’s always going to remain puzzling why Apple would not just have answered the question and put fears to rest for me and those who have reported similar concerns as mine.
That is because in iOS 13 they added the the Trust Asset Version field. This has nothing to do with being compromised! My job deals with security and trust me, this is just a part of the OS. Every OS has some implementation of a certificate bundle.Once upgraded to iOS 13, the Trust Asset Version field appeared below Trust Store on every iOS device of mine
No it didn’t. It appeared because it was added in iOS 13. It is not an indication of being compromised.prior to iOS 13 this field always appeared in conjunction with the rogue certificates (ones that didn’t start with “com.”) which would also be the day irregular behaviors began again. I witnessed this many times having factory-reset/DFU’ed my iOS devices multiple times prior to purchasing a new device. Only to see the cycle repeat on the new device within a day or two of purchase - and oftentimes never having been on Wi-Fi thinking using only cellular data might keep the device protected.
Last edited:
Thank you for the bold emphasis but I’ve read a reply similar to yours many times trying to discredit others who know something is amiss. You asked me to trust you. I don’t know you. I asked for proof. You provided none. i won’t be bullied or shamed as others have done with their “trust me” remarks. I would never have survived the past two years if I had listened to everyone who said “trust me” instead of doing the homework myself.That is because in iOS 13 they added the the Trust Asset Version field. This has nothing to do with being compromised! My job deals with security and trust me, this is just a part of the OS. Every OS has some implementation of a certificate bundle.
No it didn’t. It appeared because it was added in iOS 13. It is not an indication of being compromised.
So just to be clear unless I missed something in your comment, you did not offer any documentation or reference in an SDK manual. Your emphasis on words does not intimidate me. Nor does your assertion of your field. What will get my attention in a good way is when you can move away from “trust me” (no pun intended I assume) and back up your assertions with proof as I have done with your request and will continue to do if asked.
Look, I'm not saying you weren't compromised. What I am saying is you are barking up the wrong tree here. The appearance of the Trust Asset Version field does not indicate a compromise. It is supposed to be there on >=iOS13.Thank you for the bold emphasis but I’ve read a reply similar to yours many times trying to discredit others who know something is amiss. You asked me to trust you. I don’t know you. I asked for proof. You provided none. i won’t be bullied or shamed as others have done with their “trust me” remarks. I would never have survived the past two years if I had listened to everyone who said “trust me” instead of doing the homework myself.
So just to be clear unless I missed something in your comment, you did not offer any documentation or reference in an SDK manual. Your emphasis on words does not intimidate me. Nor does your assertion of your field. What will get my attention in a good way is when you can move away from “trust me” (no pun intended I assume) and back up your assertions with proof as I have done with your request and will continue to do if asked.
Available trusted root certificates for Apple operating systems - Apple Support
Trust Stores contains trusted root certificates that are preinstalled with iOS, iPadOS, macOS, tvOS, and watchOS.
That is normal and the current version.
![0A9A344B-6FBA-4CB8-AF48-C6D9E97BA119.png 0A9A344B-6FBA-4CB8-AF48-C6D9E97BA119.png]()
Anything strange you’re experiencing is unrelated to this.
Anything strange you’re experiencing is unrelated to this.
I can tell you, with certainty, that a Trust Asset Version of 7 is a sure fire sign of a compromised device. I can even tell you how to get your device compromised, for the skeptics out there (if you don‘t believe me, just try it—dare you): Go to purifeye.net and sign up, download, and install. This is an internet filtering company, and they do compromise your device, but the way they do it is unknown (at least to me). Even after removing the software by resetting your device will leave the compromised trust store and show a asset version of 7. They clearly are using some sort of exploit that isn’t published.
Now, that being said, you can repair your device if you’re willing to spend some money. Here’s how: (1) On a safe computer (not yours!) download iMazing. (2) Download the .ipsw of the latest iOS from Apple (the url of the link should begin with “updates-http.cdn-Apple.com” (3) Then reinstall iOS using iMazing. Your trust store will actually be fixed, and should be 12 and soon after get an OTA update to 13, as of this post.
All these ”experts” here clearly don’t seem to understand that not every exploit is PUBLISHED or well-known. Let me put it like this: if a device has software, it CAN be hacked/exploited.
For those frustrated with Apple in this regard, they have a policy as follows:
”For the protection of our customers, Apple doesn't disclose, discuss, or confirm security issues until our investigation is complete and any necessary updates are generally available.”
ref:
 support.apple.com
support.apple.com
hope this helps
Now, that being said, you can repair your device if you’re willing to spend some money. Here’s how: (1) On a safe computer (not yours!) download iMazing. (2) Download the .ipsw of the latest iOS from Apple (the url of the link should begin with “updates-http.cdn-Apple.com” (3) Then reinstall iOS using iMazing. Your trust store will actually be fixed, and should be 12 and soon after get an OTA update to 13, as of this post.
All these ”experts” here clearly don’t seem to understand that not every exploit is PUBLISHED or well-known. Let me put it like this: if a device has software, it CAN be hacked/exploited.
For those frustrated with Apple in this regard, they have a policy as follows:
”For the protection of our customers, Apple doesn't disclose, discuss, or confirm security issues until our investigation is complete and any necessary updates are generally available.”
ref:
Report a security or privacy vulnerability - Apple Support
If you believe that you have discovered a security or privacy vulnerability in an Apple product, please report it to us.
hope this helps
Purifeye is not using any exploit. From what I can tell they are installing a certificate to basically MITM your connection to provide content filtering. This certificate probably doesn’t get removed when you uninstall their software. If you install and trust someone’s certificate you need to make sure you absolutely trust them. Don’t go installing shady certificates.I can tell you, with certainty, that a Trust Asset Version of 7 is a sure fire sign of a compromised device. I can even tell you how to get your device compromised, for the skeptics out there (if you don‘t believe me, just try it—dare you): Go to purifeye.net and sign up, download, and install. This is an internet filtering company, and they do compromise your device, but the way they do it is unknown (at least to me). Even after removing the software by resetting your device will leave the compromised trust store and show a asset version of 7. They clearly are using some sort of exploit that isn’t published.
Now, that being said, you can repair your device if you’re willing to spend some money. Here’s how: (1) On a safe computer (not yours!) download iMazing. (2) Download the .ipsw of the latest iOS from Apple (the url of the link should begin with “updates-http.cdn-Apple.com” (3) Then reinstall iOS using iMazing. Your trust store will actually be fixed, and should be 12 and soon after get an OTA update to 13, as of this post.
All these ”experts” here clearly don’t seem to understand that not every exploit is PUBLISHED or well-known. Let me put it like this: if a device has software, it CAN be hacked/exploited.
For those frustrated with Apple in this regard, they have a policy as follows:
”For the protection of our customers, Apple doesn't disclose, discuss, or confirm security issues until our investigation is complete and any necessary updates are generally available.”
ref:Report a security or privacy vulnerability - Apple Support
If you believe that you have discovered a security or privacy vulnerability in an Apple product, please report it to us.support.apple.com
hope this helps
While it‘s not my style to engage in forum battles, I feel I should respond to this thread for the sake of others.Purifeye is not using any exploit. From what I can tell they are installing a certificate to basically MITM your connection to provide content filtering. This certificate probably doesn’t get removed when you uninstall their software. If you install and trust someone’s certificate you need to make sure you absolutely trust them. Don’t go installing shady certificates.
1) Yes, it is MITM attack prima facie
2) It is clearly an exploit because the damage to the certificate store survives software reset.
—a) this is not to spec for iOS devices
—b) trust ASSET version is permanently modified without complete software restore (read: this is separate and different from software reset), which is what this thread is asking about
All that aside, anyone with security concerns should follow my advice above to remedy any trust store related concerns they have.
In response to the OP and others concerned, the correct trust store info as of of 9 Jul 21 is posted at the following URL, courtesy Apple:
List of available trusted root certificates in iOS 14, iPadOS 14, macOS 11, watchOS 7, and tvOS 14
Trust Stores contains trusted root certificates that are preinstalled with iOS, iPadOS, macOS, watchOS, and tvOS.
support.apple.com
P.S.
Re: Purifeye; malwarebytes even identifies and quarantines the installer as a possible zero-day exploit. The disclosed certs added are bundled with the MDM profile. The exploit modifies the trust store
—And—
Not that it matters, I am an actual cyber sec ”expert” with nearly 15 years experience, and University degrees to go along with it.
Last edited:
hello xer010, thank you for stepping in and sharing your knowledge about this scenario. It matches my situation and need a solution from outside the current environment. I can’t even install a certificate in the firewall. I need to go to the very root.While it‘s not my style to engage in forum battles, I feel I should respond to this thread for the sake of others.
1) Yes, it is MITM attack prima facie
2) It is clearly an exploit because the damage to the certificate store survives software reset.
—a) this is not to spec for iOS devices
—b) trust ASSET version is permanently modified without complete software restore (read: this is separate and different from software reset), which is what this thread is asking about
All that aside, anyone with security concerns should follow my advice above to remedy any trust store related concerns they have.
In response to the OP and others concerned, the correct trust store info as of of 9 Jul 21 is posted at the following URL, courtesy Apple:List of available trusted root certificates in iOS 14, iPadOS 14, macOS 11, watchOS 7, and tvOS 14
Trust Stores contains trusted root certificates that are preinstalled with iOS, iPadOS, macOS, watchOS, and tvOS.support.apple.com
P.S.
Re: Purifeye; malwarebytes even identifies and quarantines the installer as a possible zero-day exploit. The disclosed certs added are bundled with the MDM profile. The exploit modifies the trust store
—And—
Not that it matters, I am an actual cyber sec ”expert” with nearly 15 years experience, and University degrees to go along with it.
Your post was helpful. Thanks.
yeah what's going on with it for real ? ive been documenting some weird **** lately thats been happening with my phone and iv stumbled into a couple things i wasn't supposed to apple is for sure up to something i dont even want to explain it on here because it sounds crazy, but if apple doesn't **** off and leave me alone soon im gonna do everything in my power to expose them and i've already showed three of there smartest whats up! bettq 16 comes with a app called feedback its super bad news, then when you find out somethings not right apple acts like there trying to help you, when its them that's been behind it the whole time. ill never buy apple again oh yeah and when that app showed up so did the trust cetificates and if you u put your phone in airplain mode and go through the settings theres a bunch of secrets just push and swipe on everything youll figure it outBro i started on 7 years ago now im a TAv12 lol and been researching since 7. I can confirm that this is NOTHING NICE. the troubles i have had to go thru with apple and even phone carrier who was forcing certs on me both refuse to answer my questions or remove the certificates that they forced on after i purchased it. I am still fighting them on it 2 years later and may have to take it to court with the substancial proof i have and other victims. Look in ur analytic data and copy paste a full page of one of them to ur notes then click find in page and type "pegasus" i want to see how many of yall have that nastyness forced into ur device as well like i do. Never be quiet we need more to stand up because the ppl who mock us who may even know way more about tech than us couldnt be anymore wrong and i have had confirmation in various forms about this issue and how bad they are trying to hide and ignore it. If it was so normal why is it so hard to find documentation by apple on it? Why wont they answer on phone bout it.? Why doesnt anyone know like actually know lots about it? But we all can find out when the last time our phones passed gas or how many minutes our sex lives contain a day/ heart beat? Come one...
-bird
Register on MacRumors! This sidebar will go away, and you'll see fewer ads.