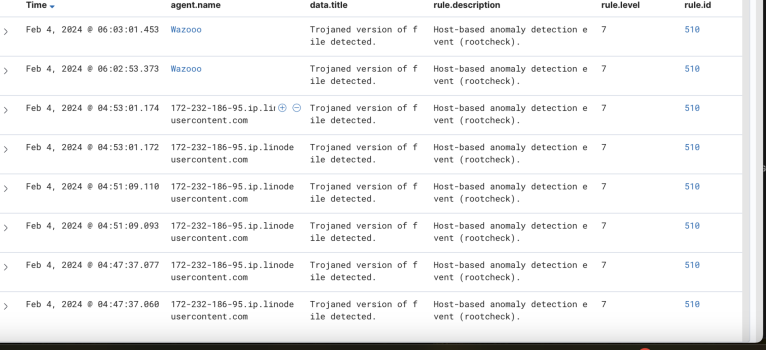
I am pretty close to putting all my devices, including my Windows machines in storage I feel like i am going through probably one of the worst cyber attacks ive personally ever heard of on a normal person, and have contacted pretty much every outlet possible and now realize that pretty much there isnt anything I can do. So I figured i would come here and maybe shed light and provide some insight into what has happened to me, and maybe it can help others in the future, or maybe someone can help me. Who knows.
A person, or a group of people ( who doesnt really matter at this point because whats done is done ) have been able to do the following to my electronics in just a matter of one week
OSX Setup:
M2 Pro Max Ultra 36gb video
M2 Air 8gb
Iphone 14 pro max
Iphone 11
1) Created 20 Network Interfaces in each of my computers and made some sort of advanced point to point tunneling system where they can move laterally through my network, including my cell phones, my wifes phone, and my son.
2) Have established pre-boot sector files that I cannot get rid of. I have been able to remove every single drive except the macos base system, which then it tells me that its in use by process 0, havent been able to figure out how to remove that
3) Have created NVRAM arguments that live past DFU firmware flashes and most of their files live within the macos base system, which is everything they need to keep persistence.. they are literally in my unifi firmware aswell
4) are able to somehow change the way native apple binaries work, as you are downloading them they are intercepted ( Not one hash or sha256 key in the past few days has matched )
5) I am most likely using some counter feit operating system because I am getting warning messages in recovery OS that i am trying to conenct to a server that is pretending to be apple.
These devices have been the joy of my life since ive bought them, and i am just lost for words that everything is basically unusable (apple just firmware flashes it and gives it back to me and puts their hands up, police dont care)
Hopefully someoen has been through this and can shed some light on what to do
A person, or a group of people ( who doesnt really matter at this point because whats done is done ) have been able to do the following to my electronics in just a matter of one week
OSX Setup:
M2 Pro Max Ultra 36gb video
M2 Air 8gb
Iphone 14 pro max
Iphone 11
1) Created 20 Network Interfaces in each of my computers and made some sort of advanced point to point tunneling system where they can move laterally through my network, including my cell phones, my wifes phone, and my son.
2) Have established pre-boot sector files that I cannot get rid of. I have been able to remove every single drive except the macos base system, which then it tells me that its in use by process 0, havent been able to figure out how to remove that
3) Have created NVRAM arguments that live past DFU firmware flashes and most of their files live within the macos base system, which is everything they need to keep persistence.. they are literally in my unifi firmware aswell
4) are able to somehow change the way native apple binaries work, as you are downloading them they are intercepted ( Not one hash or sha256 key in the past few days has matched )
5) I am most likely using some counter feit operating system because I am getting warning messages in recovery OS that i am trying to conenct to a server that is pretending to be apple.
These devices have been the joy of my life since ive bought them, and i am just lost for words that everything is basically unusable (apple just firmware flashes it and gives it back to me and puts their hands up, police dont care)
Hopefully someoen has been through this and can shed some light on what to do